Access Control System is an electronic security solution that manages entry permissions to specific areas through identity authentication using fingerprints, access cards, facial recognition, or passwords. The system ensures security by preventing unauthorized access, protecting valuable assets and critical data, while also enhancing transparency and accuracy in management, and creating a safe and efficient working environment.
When should an Access Control System (ACS) be implemented?
- Security Protection: When the organization faces risks of unauthorized access or asset loss.
- Scaling Operations: When expanding infrastructure or relocating to a new site.
- Optimized Management: When there’s a need to monitor, control access rights, and efficiently log entry and exit data.
The benefits of the Access Control System.
- Enhanced Security: Prevent unauthorized access and protect assets and data.
- Flexible Management: Easily control and grant/manage access rights remotely.
- Monitoring & Logging: Record access history to support analysis and management.
- System Integration: Connect with surveillance cameras, alarms, and building management systems.
- Improved Efficiency: Reduce administrative costs and optimize workflows.
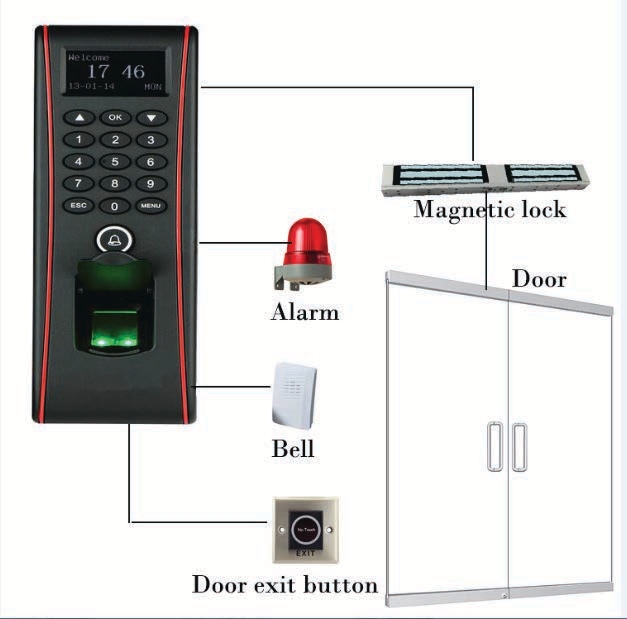
Advantages
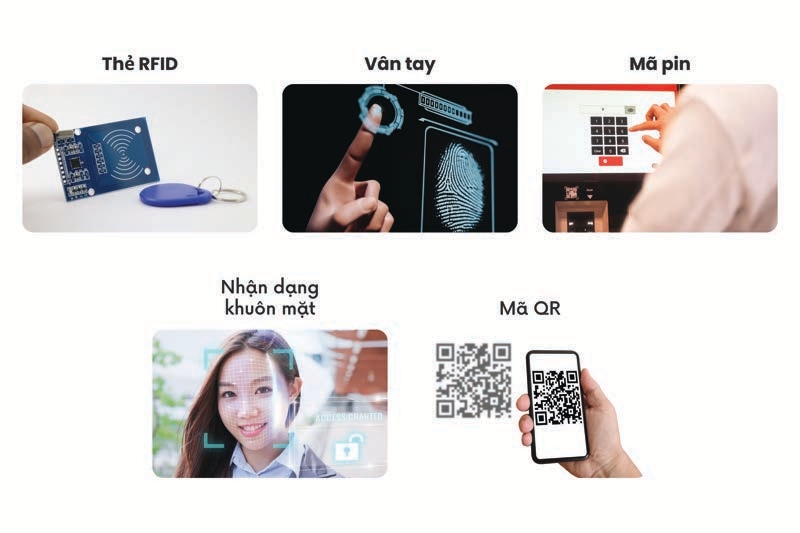
- High Security: Prevent unauthorized access and safeguard assets and data.
- Diverse Authentication Methods: Support multiple access methods such as card, fingerprint, facial recognition, and PIN code.
- Flexible Management: Easily assign access rights based on time, location, and user groups.
- Real-time Monitoring: Track entry and exit activities, quickly detect and respond to incidents.
- Easy Integration: Connect seamlessly with other systems such as surveillance cameras, alarm systems, and building management platforms.
- Cost Efficiency: Minimize the need for manual supervision and optimize operations and management.
- Improved Work Efficiency: Reduce manual checking time and streamline entry/exit processes.
Features
- Multi-factor Authentication: Supports access via card, fingerprint, facial recognition, PIN code, or QR code.
- Access Rights Management: Flexible permission settings by time, area, and user group.
- Real-time Monitoring: Track and log entry/exit history and issue alerts for incidents.
- Detailed Reporting: Provide access data and alarm events to support effective management.
- System Integration: Connect with surveillance cameras, alarm systems, and building management platforms.
- Remote Management: Control and monitor the system via mobile apps or web platforms.
Applications
- Government Buildings: Protect critical areas and restrict access based on specific authorization levels.
- Residential Buildings: Manage access for residents and visitors.
- Manufacturing Facilities: Limit access to hazardous zones or areas with valuable assets.
- Hotels: Manage room access and facility usage for guests.
- Businesses & Offices: Control employee and visitor access based on roles.
- Hospitals & Healthcare Facilities: Regulate access to patient areas and medical records.
- Libraries & Archives: Safeguard assets and control access to lending and return zones.
